Synthetic human-like fakes
When the camera does not exist, but the subject being imaged with a simulation of a (movie) camera deceives the watcher to believe it is some living or dead person it is a digital look-alike.
When it cannot be determined by human testing whether some fake voice is a synthetic fake of some person's voice, or is it an actual recording made of that person's actual real voice, it is a digital sound-alike.
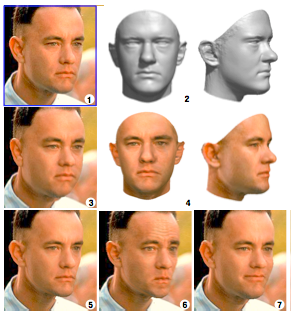
(1) Sculpting a morphable model to one single picture
(2) Produces 3D approximation
(4) Texture capture
(3) The 3D model is rendered back to the image with weight gain
(5) With weight loss
(6) Looking annoyed
(7) Forced to smile Image 2 by Blanz and Vettel – Copyright ACM 1999 – http://dl.acm.org/citation.cfm?doid=311535.311556 – Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on the first page.
Digital look-alikes
Introduction to digital look-alikes

Original picture by Debevec et al. - Copyright ACM 2000 https://dl.acm.org/citation.cfm?doid=311779.344855
In the cinemas we have seen digital look-alikes for over 15 years. These digital look-alikes have "clothing" (a simulation of clothing is not clothing) or "superhero costumes" and "superbaddie costumes", and they don't need to care about the laws of physics, let alone laws of physiology. It is generally accepted that digital look-alikes made their public debut in the sequels of The Matrix i.e. w:The Matrix Reloaded and w:The Matrix Revolutions released in 2003. It can be considered almost certain, that it was not possible to make these before the year 1999, as the final piece of the puzzle to make a (still) digital look-alike that passes human testing, the reflectance capture over the human face, was made for the first time in 1999 at the w:University of Southern California and was presented to the crème de la crème of the computer graphics field in their annual gathering SIGGRAPH 2000.[1]
“Do you think that was Hugo Weaving's left cheekbone that Keanu Reeves punched in with his right fist?”
The problems with digital look-alikes
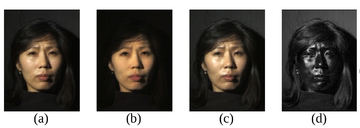
(a) Normal image in dot lighting
(b) Image of the diffuse reflection which is caught by placing a vertical polarizer in front of the light source and a horizontal in the front the camera
(c) Image of the highlight specular reflection which is caught by placing both polarizers vertically
(d) Subtraction of c from b, which yields the specular component
Images are scaled to seem to be the same luminosity.
Original image by Debevec et al. – Copyright ACM 2000 – https://dl.acm.org/citation.cfm?doid=311779.344855 – Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on the first page.
Extremely unfortunately for the humankind, organized criminal leagues, that posses the weapons capability of making believable looking synthetic pornography, are producing on industrial production pipelines synthetic terror porn[footnote 1] by animating digital look-alikes and distributing it in the murky Internet in exchange for money stacks that are getting thinner and thinner as time goes by.
These industrially produced pornographic delusions are causing great humane suffering, especially in their direct victims, but they are also tearing our communities and societies apart, sowing blind rage, perceptions of deepening chaos, feelings of powerlessness and provoke violence. This hate illustration increases and strengthens hate thinking, hate speech, hate crimes and tears our fragile social constructions apart and with time perverts humankind's view of humankind into an almost unrecognizable shape, unless we interfere with resolve.
For these reasons the bannable raw materials i.e. covert models, needed to produce this disinformation terror on the information-industrial production pipelines, should be prohibited by law in order to protect humans from arbitrary abuse by criminal parties.
List of possible naked digital look-alike attacks
- The classic "portrayal of as if in involuntary sex"-attack. (Digital look-alike "cries")
- "Sexual preference alteration"-attack. (Digital look-alike "smiles")
How to counter synthetic porn: Adequate Porn Watcher AI (transcluded)
Adequate Porn Watcher AI (APW_AI) is an w:AI and w:computer vision concept to search for any and all porn that should not be by watching and modeling all porn ever found on the w:Internet thus effectively protecting humans by exposing covert naked digital look-alike attacks and also other contraband.
Obs. #A service identical to APW_AI used to exist - FacePinPoint.com
The method and the effect
The method by which APW_AI would be providing safety and security to its users, is that they can briefly upload a model they've gotten of themselves and then the APW_AI will either say nothing matching found or it will be of the opinion that something matching found.
If people are able to check whether there is synthetic porn that looks like themselves, this causes synthetic hate-illustration industrialists' product lose destructive potential and the attacks that happen are less destructive as they are exposed by the APW_AI and thus decimate the monetary value of these disinformation weapons to the criminals.
If you feel comfortable to leave your model with the good people at the benefactor for safekeeping you get alerted and help if you ever get attacked with a synthetic porn attack.
Rules
Looking up if matches are found for anyone else's model is forbidden and this should probably be enforced with a facial w:biometric w:facial recognition system app that checks that the model you want checked is yours and that you are awake.
Definition of adequacy
An adequate implementation should be nearly free of false positives, very good at finding true positives and able to process more porn than is ever uploaded.
What about the people in the porn-industry?
People who openly do porn can help by opting-in to help in the development by providing training material and material to test the AI on. People and companies who help in training the AI naturally get credited for their help.
There are of course lots of people-questions to this and those questions need to be identified by professionals of psychology and social sciences.
History
The idea of APW_AI occurred to User:Juho Kunsola on Friday 2019-07-12. Subsequently (the next day) this discovery caused the scrapping of the plea to ban convert modeling of human appearance as that would have rendered APW_AI legally impossible.
Resources
Tools
- w:PhotoDNA is an image-identification technology used for detecting w:child pornography and other illegal content reported to the w:National Center for Missing & Exploited Children (NCMEC) as required by law.[2] It was developed by w:Microsoft Research and w:Hany Farid, professor at w:Dartmouth College, beginning in 2009. (Wikipedia)
- The w:Child abuse image content list (CAIC List) is a list of URLs and image hashes provided by the w:Internet Watch Foundation to its partners to enable the blocking of w:child pornography & w:criminally obscene adult content in the UK and by major international technology companies. (Wikipedia).
Legal
Traditional porn-blocking
Traditional porn-blocking done by w:some countries seems to use w:DNS to deny access to porn sites by checking if the domain name matches an item in a porn sites database and if it is there then it returns an unroutable address, usually w:0.0.0.0.
Topics on github.com
- Topic "porn-block" on github.com (8 repositories as of 2020-09)[1st seen in 1]
- Topic "pornblocker" on github.com (13 repositories as of 2020-09)[1st seen in 2]
- Topic "porn-filter" on github.com (35 repositories as of 2020-09)[1st seen in 3]
Curated lists and databases
- 'Awesome-Adult-Filtering-Accountability' a list at github.com curated by wesinator - a list of tools and resources for adult content/porn accountability and filtering[1st seen in 1]
- 'Pornhosts' at github.com by Import-External-Sources is a hosts-file formatted file of the w:Response policy zone (RPZ) zone file. It states itself as " a consolidated anti porn hosts file" and states is mission as "an endeavour to find all porn domains and compile them into a single hosts to allow for easy blocking of porn on your local machine or on a network."[1st seen in 1]
- 'Amdromeda blocklist for Pi-hole' at github.com by Amdromeda[1st seen in 1] lists 50MB worth of just porn host names 1 (16.6MB) 2 (16.8MB) 3 (16.9MB) (As of 2020-09)
- 'Pihole-blocklist' at github.com by mhakim[1st seen in 3] 1
- 'superhostsfile' at github.com by universalbyte is an ongoing effort to chart out "negative" hosts.[1st seen in 2]
- 'hosts' at github.com by StevenBlack is a hosts file for negative sites. It is updated constantly from these sources and it lists 559k (1.64MB) of porn and other dodgy hosts (as of 2020-09)
- 'Porn-domains' at github.com by Bon appétit was (as of 2020-09) last updated in March 2019 and lists more than 22k domains.
Porn blocking services
- w:Pi-hole - https://pi-hole.net/ - Network-wide Ad Blocking
Software for nudity detection
- 'PornDetector' consists of two python porn images (nudity) detectors at github.com by bakwc and are both written in w:Python (programming language)[1st seen in 3]. pcr.py uses w:scikit-learn and the w:OpenCV Open Source Computer Vision Library, whereas nnpcr.py uses w:TensorFlow and reaches a higher accuracy.
- 'Laravel 7 Google Vision restringe pornografia detector de faces' porn restriction app in Portuguese at github.com by thelesson that utilizes Google Vision API to help site maintainers stop users from uploading porn has been written for the for MiniBlog w:Laravel blog app.
Links regarding pornography censorship
- w:Pornography laws by region
- w:Internet pornography
- w:Legal status of Internet pornography
- w:Sex and the law
Against pornography
- Reasons for w:opposition to pornography include w:religious views on pornography, w:feminist views of pornography, and claims of w:effects of pornography, such as w:pornography addiction. (Wikipedia as of 2020-09-19)
Technical means of censorship and how to circumvent
- w:Internet censorship and w:internet censorship circumvention
- w:Content-control software (Internet filter), a common approach to w:parental control.
- w:Accountability software
- w:Employee monitoring is often automated using w:employee monitoring software
- A w:wordfilter (sometimes referred to as just "filter" or "censor") is a script typically used on w:Internet forums or w:chat rooms that automatically scans users' posts or comments as they are submitted and automatically changes or w:censors particular words or phrases. (Wikipedia as of 2020-09)
- w:Domain fronting is a technique for w:internet censorship circumvention that uses different w:domain names in different communication layers of an w:HTTPS connection to discreetly connect to a different target domain than is discernable to third parties monitoring the requests and connections. (Wikipedia 2020-09-22)
- w:Internet censorship in China and w:some tips to how to evade internet censorship in China
Countermeasures elsewhere
Partial transclusions from Organizations, studies and events against synthetic human-like fakes below
Organizations against synthetic human-like fakes
AI incident repositories
- The 'AI Incident Database' at incidentdatabase.ai was introduced on 2020-11-18 by the w:Partnership on AI.[3]
- Artificial Intelligence Algorithmic Automation Incidents Controversies at aiaaic.org[contact 1][contacted 1] was founded by Charlie Pownall. The AIAAIC repository at aiaaic.org contains tons of reporting on different problematic uses of AI. The domain name aiaaic.org was registered on Tuesday 2021-02-23.[4]. The AIAAIC repository is a free, open resource which anyone can use, copy redistribute and adapt under the terms of its CC BY 4.0 license.[5]
- The OECD.AI Policy Observatory at oecd.ai, in conjunction with the Patrick J McGovern Foundation, provide the OECD AI Incidents Monitor (AIM) at oecd.ai
- The w:Algorithmic Justice League is also accepting reports of AI harms at report.ajl.org
Help for victims of image or audio based abuse
- Cyber Civil Rights Initiative at cybercivilrights.org, a US-based NGO.[contact 2] History / Mission / Vision of cybercivilrights.org. Get help now - CCRI Safety Center at cybercivilrights.org - CCRI Image Abuse Helpline - If you are a victim of Image- Based Sexual Abuse (IBSA), please call the CCRI Image Abuse Helpline at 1-844-878-2274, which is available free of charge, 24/7.
- Existing Nonconsensual Pornography, Sextortion, and Deep Fake Laws at cybercivilrights.org
- Report Remove: Remove a nude image shared online at childline.org.uk[1st seen in 4]. Report Remove is a service for under 19 yr olds by w:Childline, a UK service by w:National Society for the Prevention of Cruelty to Children (NSPCC) and powered by technology from the w:Internet Watch Foundation. - Childline is here to help anyone under 19 in the UK with any issue they’re going through. Info on Report Remove at iwf.org.uk
Awareness and countermeasures
- The Internet Watch Foundation at iwf.org.uk[contact 3] - The w:Internet Watch Foundation is a UK charity that seeks to to minimise the availability of online sexual abuse content, specifically child sexual abuse images and videos hosted anywhere in the world and non-photographic child sexual abuse images hosted in the UK. "About us" at iwf.org.uk, "Our technology" at iwf.org.uk
- Partnership on AI at partnershiponai.org (contact form)[contact 4] is based in the USA and funded by technology companies. They provide resources and have a vast amount and high caliber of partners. See w:Partnership on AI and Partnership on AI on LinkedIn.com for more info.
- The WITNESS Media Lab at lab.witness.org by w:Witness (organization)contact form) (contact form)[contact 5], a human rights non-profit organization based out of Brooklyn, New York, is against synthetic filth actively since 2018. They work both in awareness raising as well as media forensics.
- Open-source intelligence digital forensics - How do we work together to detect AI-manipulated media? at lab.witness.org. "In February 2019 WITNESS in association with w:George Washington University brought together a group of leading researchers in media forensics and w:detection of w:deepfakes and other w:media manipulation with leading experts in social newsgathering, w:User-generated content and w:open-source intelligence (w:OSINT) verification and w:fact-checking." (website)
- Prepare, Don’t Panic: Synthetic Media and Deepfakes at lab.witness.org is a summary page for WITNESS Media Lab's ongoing work against synthetic human-like fakes. Their work was launched in 2018 with the first multi-disciplinary convening around deepfakes preparedness which lead to the writing of the report “Mal-uses of AI-generated Synthetic Media and Deepfakes: Pragmatic Solutions Discovery Convening” (dated 2018-06-11). Deepfakes and Synthetic Media: What should we fear? What can we do? at blog.witness.org
- w:Financial Coalition Against Child Pornography could be interested in taking down payment possibilities also for sites distributing non-consensual synthetic pornography.
- Reality Defender at realitydefender.ai - Enterprise-Grade Deepfake Detection Platform for many stakeholders

- Screen Actors Guild - American Federation of Television and Radio Artists - w:SAG-AFTRA (sagaftra.org contact form[contact 6] SAG-AFTRA ACTION ALERT: "Support California Bill to End Deepfake Porn" at sagaftra.org endorses California Senate Bill SB 564 introduced to the w:California State Senate by w:California w:Senator Connie Leyva in Feb 2019.
Organizations for media forensics

- w:DARPA (darpa.mil) contact form[contact 7]DARPA program: 'Media Forensics' (MediFor) at darpa.mil aims to develop technologies for the automated assessment of the integrity of an image or video and integrating these in an end-to-end media forensics platform. Archive.org first crawled their homepage in June 2016[6].
- DARPA program: 'Semantic Forensics' (SemaFor) at darpa.mil aims to counter synthetic disinformation by developing systems for detecting semantic inconsistencies in forged media. They state that they hope to create technologies that "will help identify, deter, and understand adversary disinformation campaigns". More information at w:Duke University's Research Funding database: Semantic Forensics (SemaFor) at researchfunding.duke.edu and some at Semantic Forensics grant opportunity (closed Nov 2019) at grants.gov. Archive.org first cralwed their website in November 2019[7]
- w:University of Colorado Denver's College of Arts & Media[contact 8] is the home of the National Center for Media Forensics at artsandmedia.ucdenver.edu at the w:University of Colorado Denver offers a Master's degree program, training courses and scientific basic and applied research. Faculty staff at the NCMF
- Media Forensics Hub at clemson.edu[contact 9] at the Watt Family Innovation Center of the w:Clemson University has the aims of promoting multi-disciplinary research, collecting and facilitating discussion and ideation of challenges and solutions. They provide resources, research, media forensics education and are running a Working Group on disinformation.[contact 10]
A service identical to APW_AI used to exist - FacePinPoint.com
Transcluded from FacePinPoint.com
FacePinPoint.com was a for-a-fee service from 2017 to 2021 for pointing out where in pornography sites a particular face appears, or in the case of synthetic pornography, a digital look-alike makes make-believe of a face or body appearing.[contacted 2]The inventor and founder of FacePinPoint.com, Mr. Lionel Hagege registered the domain name in 2015[8], when he set out to research the feasibility of his action plan idea against non-consensual pornography.[9] The description of how FacePinPoint.com worked is the same as Adequate Porn Watcher AI (concept)'s description.
Organizations possibly against synthetic human-like fakes
Originally harvested from the study The ethics of artificial intelligence: Issues and initiatives (.pdf) by the w:European Parliamentary Research Service, published on the w:Europa (web portal) in March 2020.[1st seen in 5]
- INSTITUTE FOR ETHICS IN ARTIFICIAL INTELLIGENCE at ieai.mcts.tum.de[contact 11] received initial funding from w:Facebook in 2019.[1st seen in 5] IEAI on LinkedIn.com
- The Institute for Ethical AI & Machine Learning at ethical.institute(contact form asks a lot of questions)[contact 12][contacted 3][1st seen in 5] The Institute for Ethical AI & Machine Learning on LinkedIn.com
- Future of Life Institute at futureoflife.org (contact form with also mailing list)[contact 14][contacted 4] received funding from private donors.[1st seen in 5] See w:Future of Life Institute for more info.
- The Japanese Society for Artificial Intelligence (JSAI) at ai-gakkai.or.jp[contact 15] Publication: Ethical guidelines.[1st seen in 5]
- AI4All at ai-4-all.org (contact form with also mailing list subscription) [contact 16][contacted 5] funded by w:Google[1st seen in 5] AI4All on LinkedIn.com
- The Future Society at thefuturesociety.org (contact form with also mailing list subscription)[contact 17][1st seen in 5]. Their activities include policy research, educational & leadership development programs, advisory services, seminars & summits and other special projects to advance the responsible adoption of Artificial Intelligence (AI) and other emerging technologies. The Future Society on LinkedIn.com
- The Ai Now Institute at ainowinstitute.org (contact form and possibility to subscribe to mailing list)[contact 18][contacted 6] at w:New York University[1st seen in 5]. Their work is licensed under a Creative Commons Attribution-NoDerivatives 4.0 International License. The Ai Now Institute on LinkedIn.com
- The Foundation for Responsible Robotics at responsiblerobotics.org (contact form)[contact 19] is based in w:Netherlands.[1st seen in 5] The Foundation for Responsible Robotics on LinkedIn.com
- AI4People at ai4people.eu (contact form)[contact 20] is based in w:Belgium is a multi-stakeholder forum.[1st seen in 5] AI4People on LinkedIn.com
- The Ethics and Governance of Artificial Intelligence Initiative at aiethicsinitiative.org is a joint project of the MIT Media Lab and the Harvard Berkman-Klein Center for Internet and Society and is based in the USA.[1st seen in 5]
- Saidot at saidot.ai is a Finnish company offering a platform for AI transparency, explainability and communication.[1st seen in 5] Saidot on LinkedIn.com
- euRobotics at eu-robotics.net is funded by the w:European Commission.[1st seen in 5]
- Centre for Data Ethics and Innovation at gov.uk, part of Department for Digital, Culture, Media & Sport is financed by the UK govt. Centre for Data Ethics and Innovation Blog at cdei.blog.gov.uk[1st seen in 5] Centre for Data Ethics and Innovation on LinkedIn.com
- ACM Special Interest Group on Artificial Intelligence at sigai.acm.org is a w:Special Interest Group on AI by ACM. 'AI Matters: A Newsletter of ACM SIGAI -blog at sigai.acm.org and the newsletter that the blog gets its contents from[1st seen in 5]
- IEEE Ethics in Action - in Autonomous and Intelligent Systems at ethicsinaction.ieee.org (mailing list subscription on website)[contact 21]
- The Center for Countering Digital Hate at counterhate.com (subscribe to mailing list on website[contact 22][contacted 7] is an international not-for-profit NGO that seeks to disrupt the architecture of online hate and misinformation with offices in London and Washington DC.
- Partnership for Countering Influence Operations (PCIO) at carnegieendowment.org (contact form)[contact 23] is a partnership by the w:Carnegie Endowment for International Peace
- UN Global Pulse at unglobalpulse.org is w:United Nations Secretary-General’s initiative on big data and artificial intelligence for development, humanitarian action, and peace.
- humane-ai.eu by Knowledge 4 All Foundation Ltd. at k4all.org[contact 24]
Services that should get back to the task at hand - FacePinPoint.com
Transcluded from FacePinPoint.com
FacePinPoint.com was a for-a-fee service from 2017 to 2021 for pointing out where in pornography sites a particular face appears, or in the case of synthetic pornography, a digital look-alike makes make-believe of a face or body appearing.[contacted 8]The inventor and founder of FacePinPoint.com, Mr. Lionel Hagege registered the domain name in 2015[10], when he set out to research the feasibility of his action plan idea against non-consensual pornography.[11] The description of how FacePinPoint.com worked is the same as Adequate Porn Watcher AI (concept)'s description.
Other essential developments
- The Montréal Declaration for a Responsible Development of Artificial Intelligence at montrealdeclaration-responsibleai.com[contact 25] and the same site in French La Déclaration de Montéal IA responsable at declarationmontreal-iaresponsable.com[1st seen in 5]
- UNI Global Union at uniglobalunion.org is based in w:Nyon, w:Switzerland and deals mainly with labor issues to do with AI and robotics.[1st seen in 5] UNI Global Union on LinkedIn.com
- European Robotics Research Network at cordis.europa.eu funded by the w:European Commission.[1st seen in 5]
- European Robotics Platform at eu-robotics.net is funded by the w:European Commission. See w:European Robotics Platform and w:List of European Union robotics projects#EUROP for more info.[1st seen in 5]
Studies against synthetic human-like fakes
Detecting deep-fake audio through vocal tract reconstruction
Detecting deep-fake audio through vocal tract reconstruction is an epic scientific work, against fake human-like voices, from the w:University of Florida in published to peers in August 2022.


The work Who Are You (I Really Wanna Know)? Detecting Audio DeepFakes Through Vocal Tract Reconstruction at usenix.org, presentation page, version included in the proceedings[12] and slides from researchers of the Florida Institute for Cybersecurity Research (FICS) at fics.institute.ufl.edu in the w:University of Florida received funding from the w:Office of Naval Research and was presented on 2022-08-11 at the 31st w:USENIX Security Symposium.
This work was done by PhD student Logan Blue, Kevin Warren, Hadi Abdullah, Cassidy Gibson, Luis Vargas, Jessica O’Dell, Kevin Butler and Professor Patrick Traynor.
The University of Florida Research Foundation Inc has filed for and received an US patent titled 'Detecting deep-fake audio through vocal tract reconstruction' registration number US20220036904A1 (link to patents.google.com) with 20 claims. The patent application was published on Thursday 2022-02-03. The patent application was approved on 2023-07-04 and has an adjusted expiration date of 2041-12-29.
Protecting world leaders against deep fakes using facial, gestural, and vocal mannerisms
- Protecting world leaders against deep fakes using facial, gestural, and vocal mannerisms is a brief report by Matyáš Boháček and Hany Farid on their recent work published on Wednesday 2022-11-23 in w:Proceedings of the National Academy of Sciences of the United States of America (PNAS). 'Protecting world leaders against deep fakes using facial, gestural, and vocal mannerisms' at pnas.org[13]
Protecting President Zelenskyy against deep fakes
- Protecting President Zelenskyy against deep fakes 'Protecting President Zelenskyy against Deep Fakes' at arxiv.org[14] by Matyáš Boháček of Johannes Kepler Gymnasium and w:Hany Farid, the dean and head of of w:Berkeley School of Information at the University of California, Berkeley. This brief paper describes their automated digital look-alike detection system and evaluate its efficacy and reliability in comparison to humans with untrained eyes. Their work provides automated evaluation tools to catch so called "deep fakes" and their motivation seems to have been to find automation armor against disinformation warfare against humans and the humanity. Automated digital media forensics is a very good idea explored by many. Boháček and Farid 2022 detection system works by evaluating both facial mannerisms as well as gestural mannerisms to detect the non-human ones from the ones that are human in origin.
Other studies against synthetic human-like fakes
- The Weaponisation of Deepfakes - Digital Deception by the Far-Right at icct.nl, an w:International Centre for Counter-Terrorism policy brief by Ella Busch and Jacob Ware. Published in December 2023.
- Increasing Threats of Deepfake Identities at dhs.gov by the w:United States Department of Homeland Security
- Deepfake Pornography and the Ethics of Non-Veridical Representations at link.springer.com, a 2023 research article, published in w:Philosophy & Technology on 2023-08-23. (paywalled)
- NONCONSENSUAL DEEPFAKES: DETECTING AND REGULATING THE RISING THREAT TO PRIVACY at digitalcommons.law.uidaho.edu by Natalie Lussier, published in Idaho Law Review January 2022
- 'Disinformation That Kills: The Expanding Battlefield Of Digital Warfare' at cbinsights.com, a 2020-10-21 research brief on disinformation warfare by w:CB Insights, a private company that provides w:market intelligence and w:business analytics services
- 'Media Forensics and DeepFakes: an overview' at arXiv.org (as .pdf at arXiv.org), an overview on the subject of digital look-alikes and media forensics published in August 2020 in Volume 14 Issue 5 of IEEE Journal of Selected Topics in Signal Processing. 'Media Forensics and DeepFakes: An Overview' at ieeexplore.ieee.org (paywalled, free abstract)
- 'DEEPFAKES: False pornography is here and the law cannot protect you' at scholarship.law.duke.edu by Douglas Harris, published in Duke Law & Technology Review - Volume 17 on 2019-01-05 by w:Duke University w:Duke University School of Law
Legal information compilations
- A Look at Global Deepfake Regulation Approaches at responsible.ai[15] April 2023 compilation and reporting by Amanda Lawson of the Responsible Artificial Intelligence Institute.
- The High Stakes of Deepfakes: The Growing Necessity of Federal Legislation to Regulate This Rapidly Evolving Technology at legaljournal.princeton.edu[16] compilation and reporting by Caroline Quirk. PLJ is Princeton’s only student-run law review.
- Exploring Legal Approaches to Regulating Nonconsensual Deepfake Pornography at techpolicy.press[17] May 2023 compilation and reporting by Kaylee Williams
- Deepfake laws: is AI outpacing legislation? at onfido.com[18] February 2024 summary and compilation by Aled Owen, Director of Global Policy at Onfido (for-profit)
- Is Deepfake Pornography Illegal? at criminaldefenselawyer.com [19] by Rebecca Pirius is a good bring-together of the current illegality/legality situation in the USA federally and state-wise. Published by w:Nolo (publisher), updated Feb 2024
- Deepfake Pornography: A Legal and Ethical Menace at tclf.in[20] October 2023 compilation and reporting by Janvhi Rastogi, published in the The Contemporary Law Forum.
More studies can be found in the SSFWIKI Timeline of synthetic human-like fakes
Search for more
Reporting against synthetic human-like fakes
- 'Researchers use facial quirks to unmask ‘deepfakes’' at news.berkeley.edu 2019-06-18 reporting by Kara Manke published in Politics & society, Research, Technology & engineering-section in Berkley News of w:UC Berkeley.
Companies against synthetic human-like fakes See resources for more.
- Cyabra.com is an AI-based system that helps organizations be on the guard against disinformation attacks[1st seen in 6]. Reuters.com reporting from July 2020.
Events against synthetic human-like fakes
Upcoming events
In reverse chronological order
Ongoing events
- 2020 - ONGOING | w:National Institute of Standards and Technology (NIST) (nist.gov) (contacting NIST) | Open Media Forensics Challenge presented in Open Media Forensics Challenge at nist.gov and Open Media Forensics Challenge (OpenMFC) at mfc.nist.gov[contact 26] - Open Media Forensics Challenge Evaluation (OpenMFC) is an open evaluation series organized by the NIST to assess and measure the capability of media forensic algorithms and systems.[21]
Past events
- 2023 | World Anti-Bullying Forum October 25-27 in North Carolina, U.S.A.
- 2022 | w:European Conference on Computer Vision in Tel Aviv, Israel
- 2022 | HotNets 2022: Twenty-First ACM Workshop on Hot Topics in Networks at conferences.sigcomm.org - November 14-15, 2022 — Austin, Texas, USA. Presented at HotNets 2022 was a very interesting paper on 'Global Content Revocation on the Internet: A Case Study in Technology Ecosystem Transformation' at farid.berkeley.edu
- 2022 | INTERSPEECH 2022 at interspeech2022.org organized by w:International Speech Communication Association was held on 18-22 September 2022 in Korea. The work 'Attacker Attribution of Audio Deepfakes' at arxiv.org was presented there
- 2022 | Technologies of Deception at law.yale.edu, a conference hosted by the w:Information Society Project (ISP) was held at Yale Law School in New Haven, Connecticut, on March 25-26, 2022[22]
- 2021 | w:Conference on Neural Information Processing Systems NeurIPS 2021 at neurips.cc, was held virtually in December 2021. I haven't seen any good tech coming from there in 2021. On the problematic side w:StyleGAN3 was presented there.
- 2021 | w:Conference on Computer Vision and Pattern Recognition (CVPR) 2021 CVPR 2021 at cvpr2021.thecvf.com
- CVPR 2021 research areas visualization by Joshua Preston at public.tableau.com
- 2021 'Workshop on Media Forensics' in CVPR 2021 at sites.google.com, a June 2021 workshop at the Conference on Computer Vision and Pattern Recognition.
- 2020 | CVPR 2020 | 2020 Conference on Computer Vision and Pattern Recognition: 'Workshop on Media Forensics' at sites.google.com, a June 2020 workshop at the Conference on Computer Vision and Pattern Recognition.
- 2020 | The winners of the Deepfake Detection Challenge reach 82% accuracy in detecting synthetic human-like fakes[23]
- 2020 | You Don't Say: An FTC Workshop on Voice Cloning Technologies at ftc.gov was held on Tuesday 2020-01-28 - reporting at venturebeat.com
- 2019 | At the annual Finnish w:Ministry of Defence's Scientific Advisory Board for Defence (MATINE) public research seminar, a research group presented their work 'Synteettisen median tunnistus'' at defmin.fi (Recognizing synthetic media). They developed on earlier work on how to automatically detect synthetic human-like fakes and their work was funded with a grant from MATINE.
- 2019 | w:NeurIPS 2019 | w:Facebook, Inc. "Facebook AI Launches Its Deepfake Detection Challenge" at spectrum.ieee.org w:IEEE Spectrum. More reporting at "Facebook, Microsoft, and others launch Deepfake Detection Challenge" at venturebeat.com
- 2017-2020 | NIST | NIST: 'Media Forensics Challenge' (MFC) at nist.gov, an iterative research challenge by the w:National Institute of Standards and Technology the evaluation criteria for the 2019 iteration are being formed. Succeeded by the Open Media Forensics Challenge.
- 2018 | w:European Conference on Computer Vision (ECCV) ECCV 2018: 'Workshop on Objectionable Content and Misinformation' at sites.google.com, a workshop at the 2018 w:European Conference on Computer Vision in w:Munich had focus on objectionable content detection e.g. w:nudity, w:pornography, w:violence, w:hate, w:children exploitation and w:terrorism among others and to address misinformation problems when people are fed w:disinformation and they punt it on as misinformation. Announced topics included w:image/video forensics, w:detection/w:analysis/w:understanding of w:fake images/videos, w:misinformation detection/understanding: mono-modal and w:multi-modal, adversarial technologies and detection/understanding of objectionable content
- 2018 | NIST NIST 'Media Forensics Challenge 2018' at nist.gov was the second annual evaluation to support research and help advance the state of the art for image and video forensics technologies – technologies that determine the region and type of manipulations in imagery (image/video data) and the phylogenic process that modified the imagery.
- 2017 | NIST NIST 'Nimble Challenge 2017' at nist.gov
- 2016 | Nimble Challenge 2016 - NIST released the Nimble Challenge’16 (NC2016) dataset as the MFC program kickoff dataset, (where NC is the former name of MFC). [24]
Sources for technologies

|
| A map of technologies courtesy of Samsung Next, linked from 'Why it’s time to change the conversation around synthetic media' at venturebeat.com[1st seen in 7] |
See also
 Image 1: Separating specular and diffuse reflected light (a) Normal image in dot lighting (b) Image of the diffuse reflection which is caught by placing a vertical polarizer in front of the light source and a horizontal in the front the camera (c) Image of the highlight specular reflection which is caught by placing both polarizers vertically (d) The difference of c and b yields the specular highlight component Images are scaled to seem to be the same luminosity. Original image by Debevec et al. – Copyright ACM 2000 – https://dl.acm.org/citation.cfm?doid=311779.344855 – Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on the first page. |
Biblical connection - Revelation 13 and Daniel 7, wherein Daniel 7 and Revelation 13 we are warned of this age of industrial filth. In Revelation 19:20 it says that the beast is taken prisoner, can we achieve this without 'APW_AI?  'Saint John on Patmos' pictures w:John of Patmos on w:Patmos writing down the visions to make the w:Book of Revelation 'Saint John on Patmos' from folio 17 of the w:Très Riches Heures du Duc de Berry (1412-1416) by the w:Limbourg brothers. Currently located at the w:Musée Condé 40km north of Paris, France. |
References
- ↑ Debevec, Paul (2000). "Acquiring the reflectance field of a human face". Proceedings of the 27th annual conference on Computer graphics and interactive techniques - SIGGRAPH '00. ACM. pp. 145–156. doi:10.1145/344779.344855. ISBN 978-1581132083. Retrieved 2017-05-24.
- ↑ "Microsoft tip led police to arrest man over child abuse images". w:The Guardian. 2014-08-07.
- ↑ https://www.partnershiponai.org/aiincidentdatabase/
- ↑ whois aiaaic.org
- ↑ https://charliepownall.com/ai-algorithimic-incident-controversy-database/
- ↑ https://web.archive.org/web/20160630154819/https://www.darpa.mil/program/media-forensics
- ↑ https://web.archive.org/web/20191108090036/https://www.darpa.mil/program/semantic-forensics November
- ↑ whois facepinpoint.com
- ↑ https://www.facepinpoint.com/aboutus
- ↑ whois facepinpoint.com
- ↑ https://www.facepinpoint.com/aboutus
- ↑ Blue, Logan; Warren, Kevin; Abdullah, Hadi; Gibson, Cassidy; Vargas, Luis; O’Dell, Jessica; Butler, Kevin; Traynor, Patrick (August 2022). "Detecting deep-fake audio through vocal tract reconstruction". Proceedings of the 31st USENIX Security Symposium: 2691–2708. ISBN 978-1-939133-31-1. Retrieved 2022-10-06.
- ↑ Boháček, Matyáš; Farid, Hany (2022-11-23). "Protecting world leaders against deep fakes using facial, gestural, and vocal mannerisms". w:Proceedings of the National Academy of Sciences of the United States of America. 119 (48). doi:10.1073/pnas.221603511. Retrieved 2023-01-05.
- ↑ Boháček, Matyáš; Farid, Hany (2022-06-14). "Protecting President Zelenskyy against Deep Fakes". arXiv:2206.12043 [cs.CV].
- ↑ Lawson, Amanda (2023-04-24). "A Look at Global Deepfake Regulation Approaches". responsible.ai. Responsible Artificial Intelligence Institute. Retrieved 2024-02-14.
- ↑ Quirk, Caroline (2023-06-19). "The High Stakes of Deepfakes: The Growing Necessity of Federal Legislation to Regulate This Rapidly Evolving Technology". legaljournal.princeton.edu. Princeton Legal Journal. Retrieved 2024-02-14.
- ↑ Williams, Kaylee (2023-05-15). "Exploring Legal Approaches to Regulating Nonconsensual Deepfake Pornography". techpolicy.press. Retrieved 2024-02-14.
- ↑ Owen, Aled (2024-02-02). "Deepfake laws: is AI outpacing legislation?". onfido.com. Onfido. Retrieved 2024-02-14.
- ↑ Pirius, Rebecca (2024-02-07). "Is Deepfake Pornography Illegal?". Criminaldefenselawyer.com. w:Nolo (publisher). Retrieved 2024-02-22.
- ↑ Rastogi, Janvhi (2023-10-16). "Deepfake Pornography: A Legal and Ethical Menace". tclf.in. The Contemporary Law Forum. Retrieved 2024-02-14.
- ↑ https://www.nist.gov/itl/iad/mig/open-media-forensics-challenge
- ↑ https://law.yale.edu/isp/events/technologies-deception
- ↑ https://venturebeat.com/2020/06/12/facebook-detection-challenge-winners-spot-deepfakes-with-82-accuracy/
- ↑ https://www.nist.gov/itl/iad/mig/open-media-forensics-challenge
1st seen in
- ↑ 1.0 1.1 1.2 1.3 Seen first in https://github.com/topics/porn-block, meta for actual use. The topic was stumbled upon.
- ↑ 2.0 2.1 Seen first in https://github.com/topics/pornblocker Saw this originally when looking at https://github.com/topics/porn-block Topic
- ↑ 3.0 3.1 3.2 Seen first in https://github.com/topics/porn-filter Saw this originally when looking at https://github.com/topics/porn-block Topic
- ↑ https://www.iwf.org.uk/our-technology/report-remove/
- ↑ 5.00 5.01 5.02 5.03 5.04 5.05 5.06 5.07 5.08 5.09 5.10 5.11 5.12 5.13 5.14 5.15 5.16 5.17 5.18 5.19
"The ethics of artificial intelligence: Issues and initiatives" (PDF). w:Europa (web portal). w:European Parliamentary Research Service. March 2020. Retrieved 2021-02-17.
This study deals with the ethical implications and moral questions that arise from the development and implementation of artificial intelligence (AI) technologies.
- ↑ https://www.reuters.com/article/us-cyber-deepfake-activist/deepfake-used-to-attack-activist-couple-shows-new-disinformation-frontier-idUSKCN24G15E
- ↑ venturebeat.com found via some Facebook AI & ML group or page yesterday. Sorry, don't know precisely right now.
Digital sound-alikes
Living people can defend[footnote 2] themselves against digital sound-alike by denying the things the digital sound-alike says if they are presented to the target, but dead people cannot. Digital sound-alikes offer criminals new disinformation attack vectors and wreak havoc on provability.
Timeline of digital sound-alikes
- In 2016 w:Adobe Inc.'s Voco, an unreleased prototype, was publicly demonstrated in 2016. (View and listen to Adobe MAX 2016 presentation of Voco)
- In 2016 w:DeepMind's w:WaveNet owned by w:Google also demonstrated ability to steal people's voices
- In 2018 Conference on Neural Information Processing Systems the work 'Transfer Learning from Speaker Verification to Multispeaker Text-To-Speech Synthesis' (at arXiv.org) was presented. The pre-trained model is able to steal voices from a sample of only 5 seconds with almost convincing results
- As of 2019 Symantec research knows of 3 cases where digital sound-alike technology has been used for crimes.[1]
'Transfer Learning from Speaker Verification to Multispeaker Text-To-Speech Synthesis' 2018 by Google Research (external transclusion)
The Iframe below is transcluded from 'Audio samples from "Transfer Learning from Speaker Verification to Multispeaker Text-To-Speech Synthesis"' at google.gituhub.io, the audio samples of a sound-like-anyone machine presented as at the 2018 w:NeurIPS conference by Google researchers.
Documented digital sound-alike attacks
- 'An artificial-intelligence first: Voice-mimicking software reportedly used in a major theft', a 2019 Washington Post article
Possible legal response: Outlawing digital sound-alikes (transcluded)
Transcluded from Juho's proposal on banning digital sound-alikes
Example of a hypothetical 4-victim digital sound-alike attack
A very simple example of a digital sound-alike attack is as follows:
Someone puts a digital sound-alike to call somebody's voicemail from an unknown number and to speak for example illegal threats. In this example there are at least two victims:
- Victim #1 - The person whose voice has been stolen into a covert model and a digital sound-alike made from it to frame them for crimes
- Victim #2 - The person to whom the illegal threat is presented in a recorded form by a digital sound-alike that deceptively sounds like victim #1
- Victim #3 - It could also be viewed that victim #3 is our law enforcement systems as they are put to chase after and interrogate the innocent victim #1
- Victim #4 - Our judiciary which prosecutes and possibly convicts the innocent victim #1.
Thus it is high time to act and to criminalize the covert modeling of human appearance and voice!
Examples of speech synthesis software not quite able to fool a human yet
Some other contenders to create digital sound-alikes are though, as of 2019, their speech synthesis in most use scenarios does not yet fool a human because the results contain tell tale signs that give it away as a speech synthesizer.
- Lyrebird.ai (listen)
- CandyVoice.com (test with your choice of text)
- Merlin, a w:neural network based speech synthesis system by the Centre for Speech Technology Research at the w:University of Edinburgh
The below video 'This AI Clones Your Voice After Listening for 5 Seconds' by '2 minute papers' describes the voice thieving machine presented by Google Research in NeurIPS 2018.

Media perhaps about synthetic human-like fakes
This is a chronological listing of media that are probably to do with synthetic human-like fakes.
6th century BC

Daniel 7, Daniel's vision of the three beasts Dan 7:1-6 and the fourth beast Dan 7:7-8 from the sea and the Ancient of DaysDan 7:9-10
- w:6th century BC | scripture | w:Daniel (biblical figure) was in w:Babylonian captivity when he had his visions where God warned us of synthetic human-like fakes first.
- His testimony was put into written form in the #3rd century BC.
3rd century BC
- w:3rd century BC | scripture | The w:Book of Daniel was put in writing.
- See Biblical explanation - The books of Daniel and Revelations § Daniel 7. Caution to reader: contains explicit written information about the beasts.
Footnotes
- ↑ It is terminologically more precise, more inclusive and more useful to talk about 'synthetic terror porn', if we want to talk about things with their real names, than 'synthetic rape porn', because also synthesizing recordings of consentual looking sex scenes can be terroristic in intent.
- ↑ Whether a suspect can defend against faked synthetic speech that sounds like him/her depends on how up-to-date the judiciary is. If no information and instructions about digital sound-alikes have been given to the judiciary, they likely will not believe the defense of denying that the recording is of the suspect's voice.
References
Cite error: <ref> tags exist for a group named "contact", but no corresponding <references group="contact"/> tag was found
Cite error: <ref> tags exist for a group named "contacted", but no corresponding <references group="contacted"/> tag was found